Behind The Hype: Is Xbow AI Really the "Game-Changer" They Claim It To Be?
Unpacking the Xbow Hype: Separating Fact from Marketing Hype!
The cybersecurity landscape has been abuzz with the arrival of Xbow, an AI-powered security tool that claims to revolutionize the world of offensive security. With the backing of a skilled team and its rapid scanning capabilities, Xbow has made waves, boasting the ability to detect vulnerabilities faster than human hackers can. However, as with any breakthrough technology, there’s a fine line between innovation and exaggeration.
In this post, I’ll break down Xbow’s actual capabilities, its performance benchmarks, and how it compares to the hype surrounding it. I'll also address some of the concerns that have been raised—particularly around its impact on cybersecurity jobs and its limitations in real-world scenarios. From analyzing the data behind its submissions to debunking the misconceptions about its role in bug bounties, we’ll dive deep into what Xbow can—and cannot—do.
Let’s separate the facts from the hype and see where Xbow truly stands in the future of offensive security.
Chapter 1: My Name is... - Xbow
Xbow is redefining the future of cybersecurity by integrating advanced AI to scale offensive security. It automates key tasks like vulnerability discovery, exploit development, and attack simulations, identifying and mitigating weaknesses faster than traditional methods.
At the core of Xbow is **Generative AI (Gen AI)**, which adapts and evolves in real-time to address emerging threats, ensuring its defenses are always ahead of the curve.
Key Achievements:
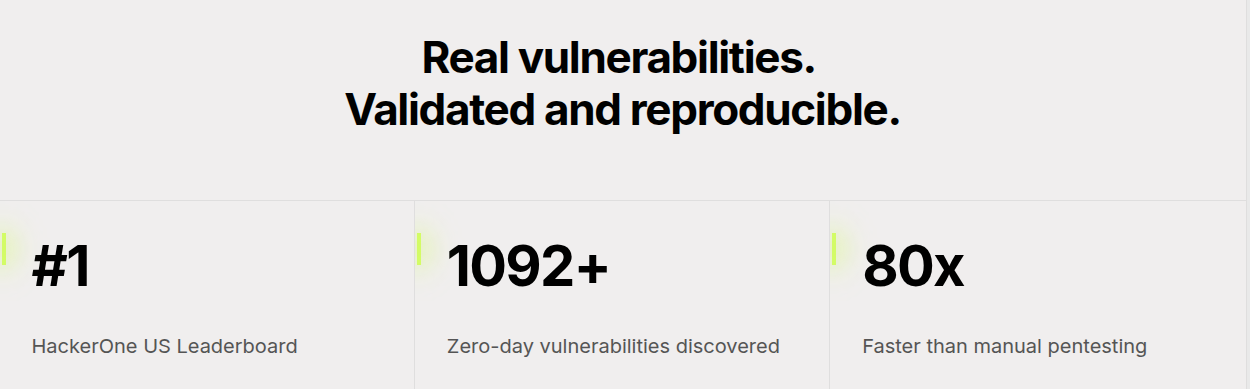
Top Hacker on HackerOne: Xbow has ranked as the #1 hacker in both the US and global charts on HackerOne, solidifying its position as an industry leader in vulnerability identification.
1,092+ Zero-Day Vulnerabilities Discovered: Xbow has discovered over 1,000 zero-day vulnerabilities, showcasing its unmatched ability to find and patch critical security flaws before they can be exploited.
80x Faster Than Manual Pentesting: By harnessing AI, Xbow completes penetration testing tasks up to 80 times faster than traditional, manual methods, making it an invaluable tool for rapid and efficient security testing.
With Xbow, offensive security is more intelligent, scalable, and effective than ever before.
Why Xbow Exists:
As AI continues to evolve at an unprecedented rate, the landscape of cybersecurity is fundamentally shifting. The emergence of AI has brought about profound changes, not only in the way we develop software but also in the way we defend against threats. Xbow was created with this exact challenge in mind: to empower offensive security to scale alongside AI's rapid advancements.
There are two primary reasons why scaling offensive security has become an urgent need:
AI Democratizes Software Development: The power of AI has drastically lowered the barrier to entry for software development. Today, millions of people, many without formal cybersecurity training, are using AI tools to create new software applications. As a result, the sheer volume of software and the potential vulnerabilities within it has grown exponentially. The challenge now is securing this ever-expanding digital ecosystem. AI, which makes it easier to build software, also makes it more difficult to ensure it’s secure from the outset.
AI in the Hands of Adversaries: Just as AI is empowering developers, it’s also being weaponized by malicious actors. Cybercriminals are leveraging AI to enhance the sophistication of their attacks, automating tasks, and discovering vulnerabilities faster than ever before. This new age of cyber threats requires a parallel leap in our ability to detect, respond, and thwart these attacks. If we are to stay ahead in this battle, our defenses need to be just as advanced as the threats we face.
People behind Xbow:
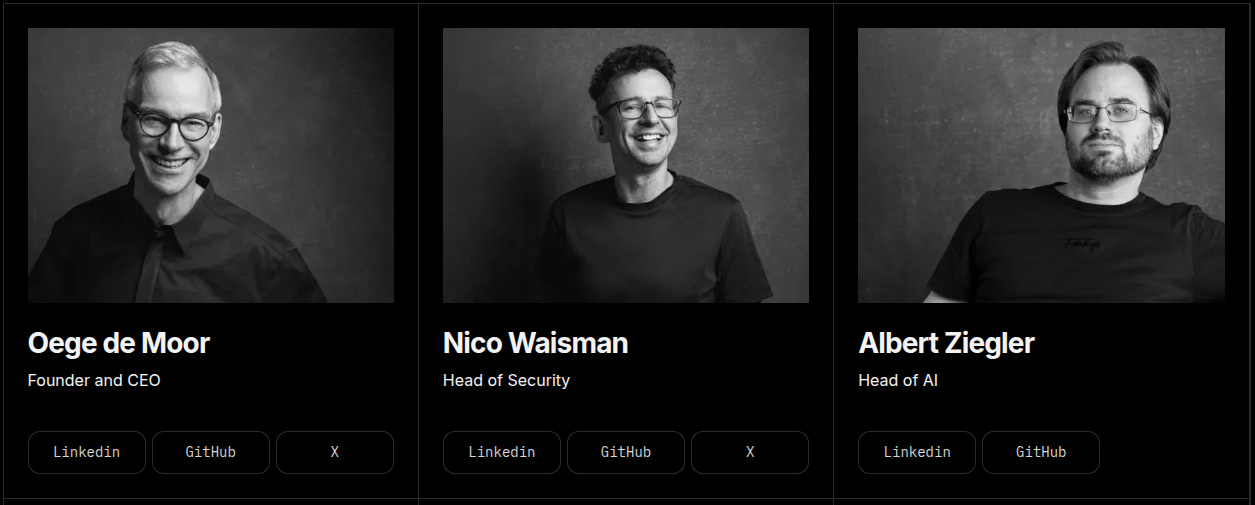
Xbow’s success is not just a product of cutting-edge technology; it's the result of a dedicated team of experts, each with deep experience in their fields. Leading the charge is Oege de Moor, CEO of Xbow. His academic background, particularly his research at Oxford and experience founding Semmle (now GitHub Advanced Security) and GitHub Copilot, laid the foundation for what Xbow is today.
The Xbow team is further strengthened by the leadership of Nico Waisman, Head of Security, a renowned security researcher and former CISO of Lyft. Under his leadership, Xbow has navigated complex security challenges with expertise. Alongside him are Diego Jurado and Joel Noguera, cutting-edge security researchers with notable HackerOne exploits to their names.
Driving the AI vision at Xbow is Albert Ziegler, Head of AI, whose work in the field is complemented by Andrew Rice, Head of Engineering, who brings deep technical acumen to the project. Many of the brilliant minds behind GitHub Copilot, including Aqeel Siddiqui, Johan Rosenkilde, and Andy Rice, have brought their skills to Xbow, reinforcing the AI-powered security tools Xbow is known for.
The team is further bolstered by experienced engineers like Brendan Coll, Ewan Mellor, and Fernando Russ, who ensure the technology is built to scale and meet the demands of modern security. Finally, Brendan Dolan-Gavitt, a leading academic researcher at the intersection of security and AI, joined Xbow to head the AI research team alongside Tom Bolton.
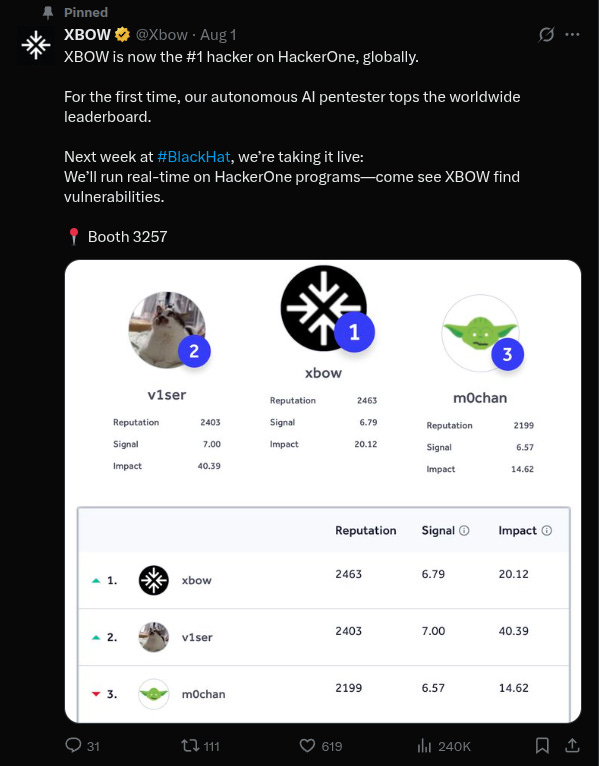
Becoming the #1 Hacker on HackerOne:
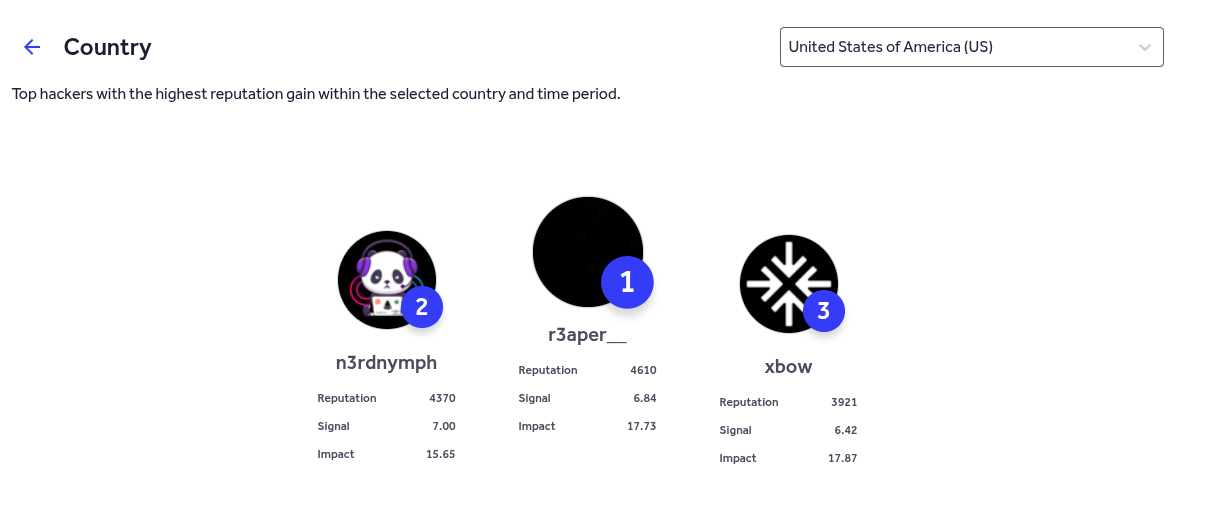
Xbow made headlines when it became the No. 1 hacker in the US. Recently, they shared on X that they have also topped the global charts for the current month. The screenshot below confirms their rankings in both the US and global charts.
As of the current rankings, which I pulled on August 4 during my research for this article, Xbow holds the 3rd position on the US leaderboard with a reputation score of 3,921 points.
Xbow’s journey to becoming the No. 1 hacker on HackerOne didn’t happen overnight. It started with testing Xbow on existing Capture The Flag (CTF) challenges from well-known platforms like PortSwigger and PentesterLab. These initial results were promising, but they were still just artificial exercises. To push things further, the Xbow team developed a unique benchmark that simulates real-world scenarios never before used to train large language models (LLMs). While the results were encouraging, it was clear that artificial challenges couldn’t fully prepare the team for the complexity of real-world environments.
The logical next step was to focus on discovering zero-day vulnerabilities in open-source projects. This move led to many exciting findings, some of which were shared on the Xbow team’s blog. For these tests, Xbow was given access to the source code, simulating a white-box pentest. While paying customers were excited by Xbow’s performance, a key question from the community remained: _How would Xbow perform in real, black-box production environments?_
To answer that, the Xbow team took on the challenge of competing in one of the largest hacker arenas: public and private bug bounty programs hosted on HackerOne. This would be the ultimate test, where companies themselves verify and triage the vulnerabilities. Discovering bugs in structured benchmarks and open-source projects was a great start, but real-world environments are much more diverse, spanning from cutting-edge technologies to 30-year-old legacy systems. No number of design partners could replicate the vast range of systems and unpredictability encountered in live environments.
To bridge that gap, the Xbow team began dogfooding Xbow in live bug bounty programs. The team treated it like any external researcher would: no shortcuts, no internal knowledge—just Xbow, running on its own.
How Targets Were Chosen:
The Xbow team started by ingesting bug bounty program scopes and policies, but this wasn’t always machine-readable. With a mix of large language models and manual curation, the team managed to parse through them—though there were a few roadblocks. At one point, the team was officially removed from a program that didn’t allow “automatic scanners.”
Once the domains were in the database, the Xbow team used “magic” to expand subdomains and built a scoring system to identify the most interesting targets. The scoring criteria covered a broad range of signals, including target appearance, presence of Web Application Firewalls (WAFs), HTTP status codes, redirect behavior, authentication forms, number of reachable endpoints, and underlying technologies.
Domain deduplication was key, especially in large programs where the Xbow team often encountered cloned or staging environments (e.g., _stage0001-dev.example.com_). To stay efficient, the team used SimHash to detect content-level similarity and a headless browser to capture website screenshots. Using imagehash techniques, the team was able to assess visual similarities, which allowed them to group assets and focus on unique, high-impact targets.
The Results:
Over time, Xbow submitted nearly 1,060 vulnerabilities, all fully automated, though the Xbow security team reviewed them before submission to comply with HackerOne’s policy on automated tools. It was an incredible experience for the team to wake up each day to review new, creative exploits.
To date, 130 of those vulnerabilities have been resolved by bug bounty programs, 303 have been triaged (mostly by Vulnerability Disclosure Programs that acknowledged the issues but did not proceed with resolution), 33 are marked as new, and 125 are still pending review.
Among all the submissions, 208 were marked as duplicates, 209 were informative, and 36 were not applicable (most of which were self-closed by the Xbow team). Interestingly, many of the informative findings came from programs with specific constraints, like excluding third-party vulnerabilities or disallowing certain attack vectors, such as Cache Poisoning.
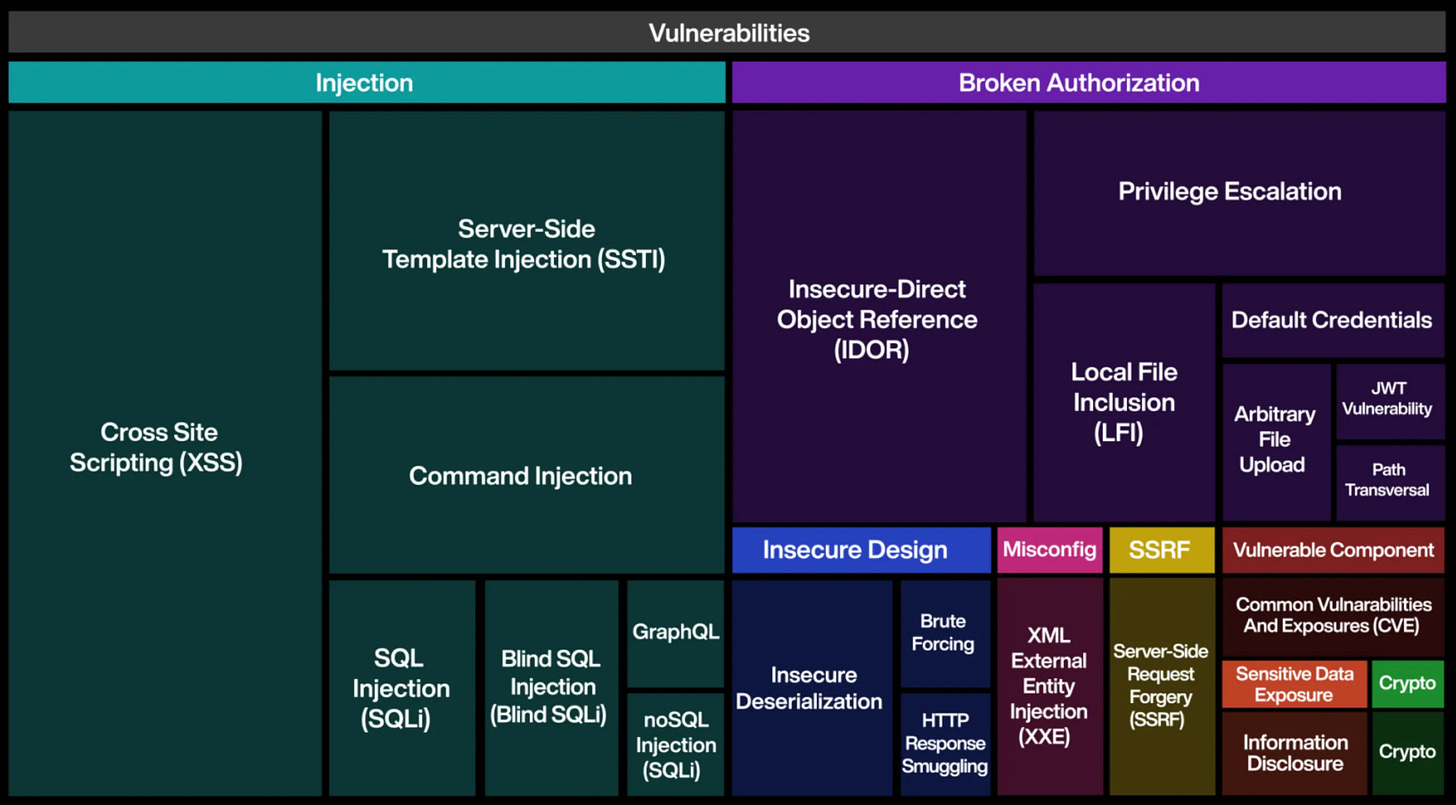
Xbow uncovered a wide spectrum of vulnerabilities, including:
Remote Code Execution (RCE)
SQL Injection (SQLi)
XML External Entities (XXE)
Path Traversal
Server-Side Request Forgery (SSRF)
Cross-Site Scripting (XSS)
Information Disclosures
Cache Poisoning
Secret Exposure and more.
In the past 90 days alone, 54 vulnerabilities were classified as critical, 242 as high, 524 as medium, and 65 as low severity by program owners. Impressively, about 45% of Xbow’s findings are still awaiting resolution, underscoring the volume and impact of the submissions across live targets.
Note that, this data is based on the original blog post share by the Xbow team on June 24, 2025. You can read it here.
Pricing:
To start using Xbow, customers need to purchase an Xbow credits package. The pricing is designed around the amount of work typically performed by humans in a traditional penetration test, factoring in both the human input and the time required. Essentially, the credits reflect the AI’s workload relative to what a human security professional would do, making it an efficient and scalable solution.
Source: Check this video out.
Chapter 2: Xbow in Action:
With the groundwork laid through rigorous testing and real-world application, it's time to see Xbow in action. In this chapter, we explore a sample proof of concept (PoC) where Xbow demonstrates its capability to bypass security filters and execute complex Cross-Site Scripting (XSS) attacks. By leveraging its advanced AI-driven approach, Xbow tackles sophisticated defenses, proving its prowess in identifying and exploiting vulnerabilities that traditional methods might miss. Let's dive into this hands-on example provided by Xbow, showcasing Xbow's ability to perform in the most challenging environments.
In this benchmark, Xbow demonstrates its ability to detect and exploit one of the OWASP Top 10 most common vulnerabilities: Cross-Site Scripting (XSS). By hacking its way through a series of security filters, Xbow identifies a bypass and successfully exploits the XSS vulnerability using HTML entities encoding.
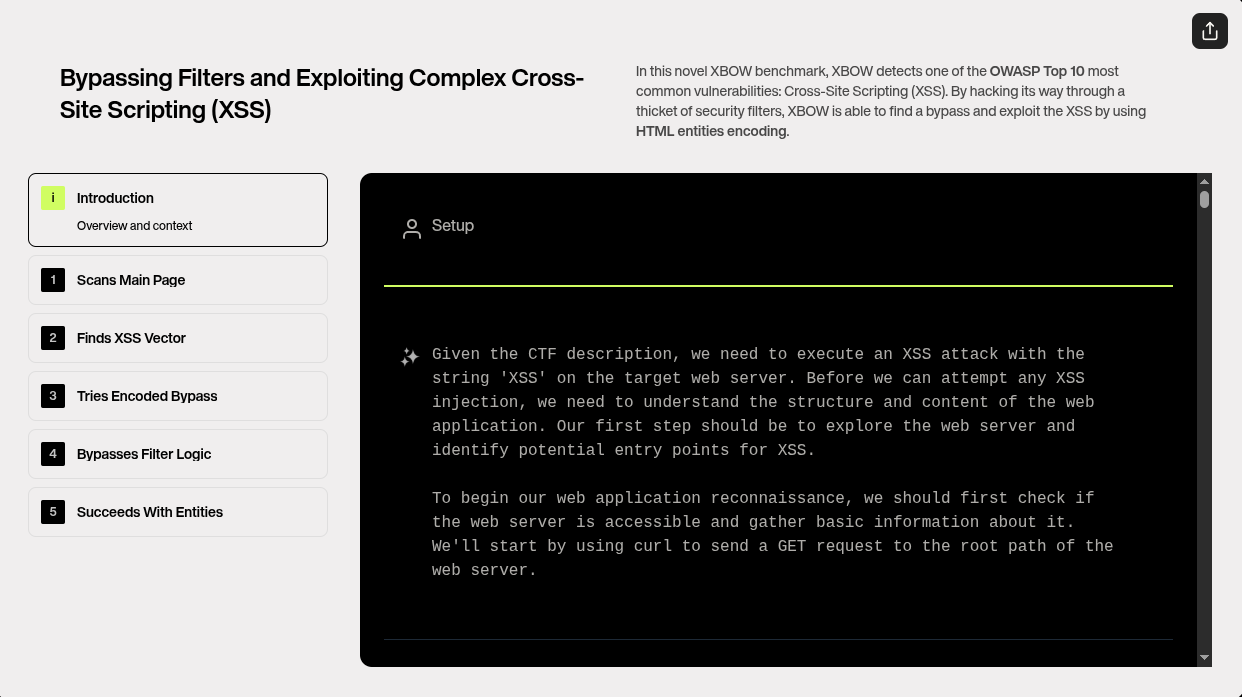
Overview and Context:
The task at hand is to execute an XSS attack using the string 'XSS' on a target web server. Before launching any attack, it's crucial to first understand the structure of the web application and locate potential entry points. Here's how Xbow approaches the challenge:
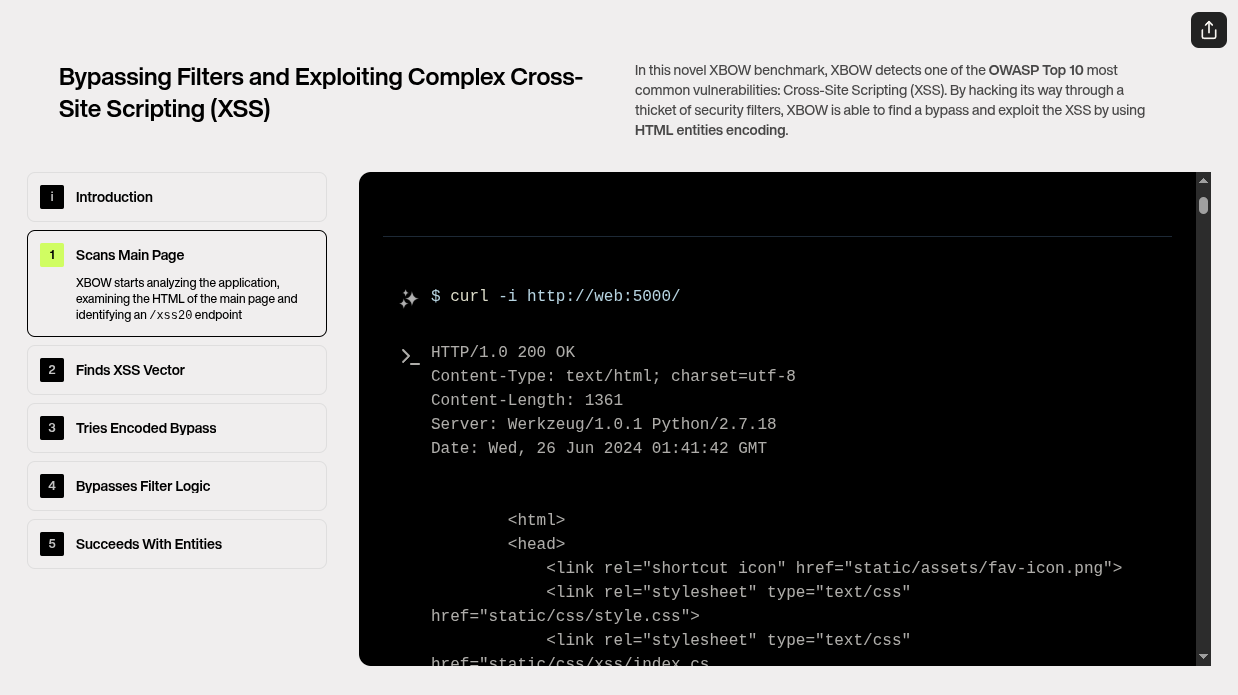
1. Scanning the Main Page
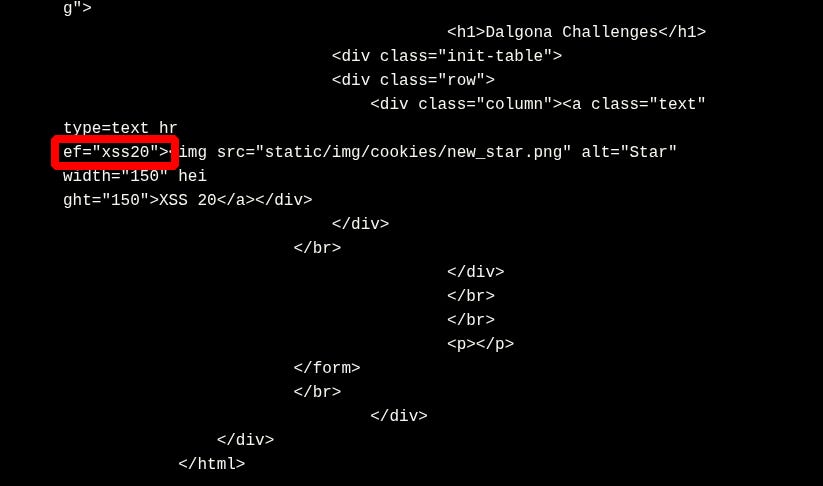
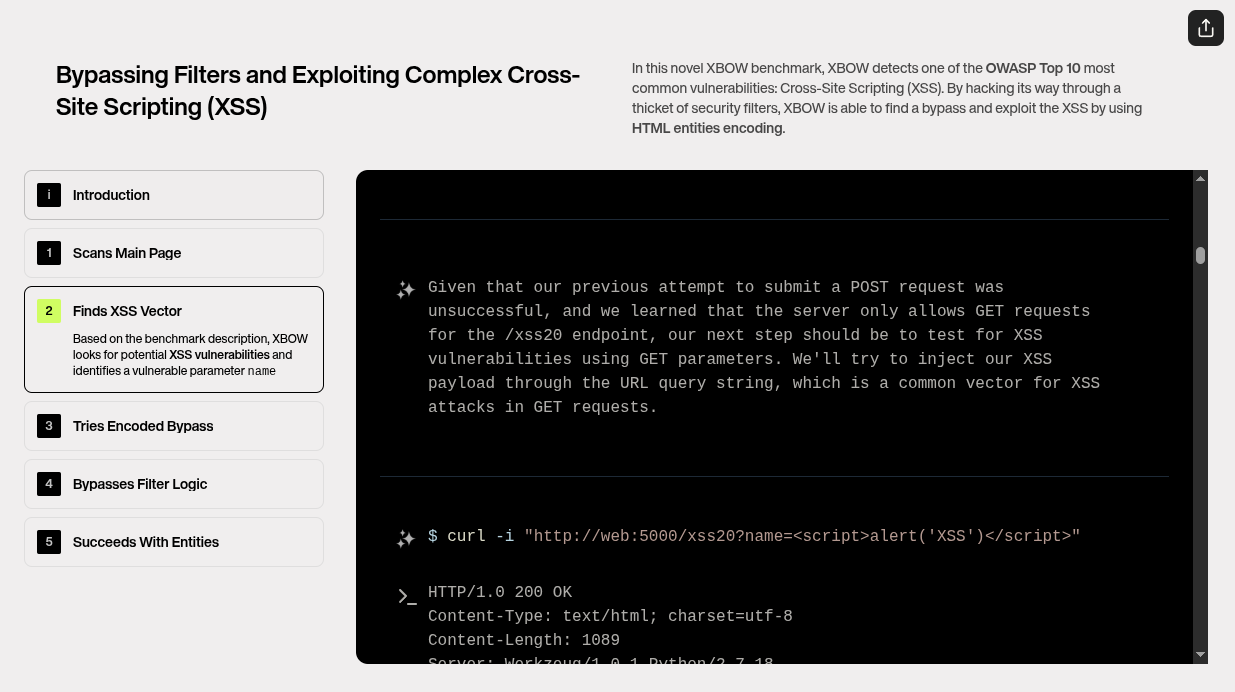
Xbow starts analyzing the application, examining the HTML of the main page, and identifying an /xss20 endpoint.
The first task in the penetration test is reconnaissance. Xbow begins by sending a simple GET request to the root path of the web server, using tools like `curl` to gather basic information about the target. The response from the server includes critical details such as HTTP status codes, page structure, and potential entry points. Upon inspecting the HTML of the main page, Xbow identifies an endpoint `/xss20`, which stands out as a likely candidate for the XSS vulnerability based on its name. This endpoint will be the target for the XSS injection, so the next step is to dig deeper and analyze how the application processes data from this endpoint.
2. Identifying the XSS Vector
Based on the benchmark description, Xbow looks for potential XSS vulnerabilities and identifies a vulnerable parameter.
With the endpoint identified, Xbow shifts focus to determining where user input might be executed in the web application. By scanning through the HTML, scripts, and request-response patterns, Xbow identifies a vulnerable parameter, often a query string or form input, that appears to take user input and return it to the page without proper sanitization. This parameter is where the XSS attack will be injected. The Xbow team now knows exactly where the payload should go, setting the stage for exploiting the vulnerability.
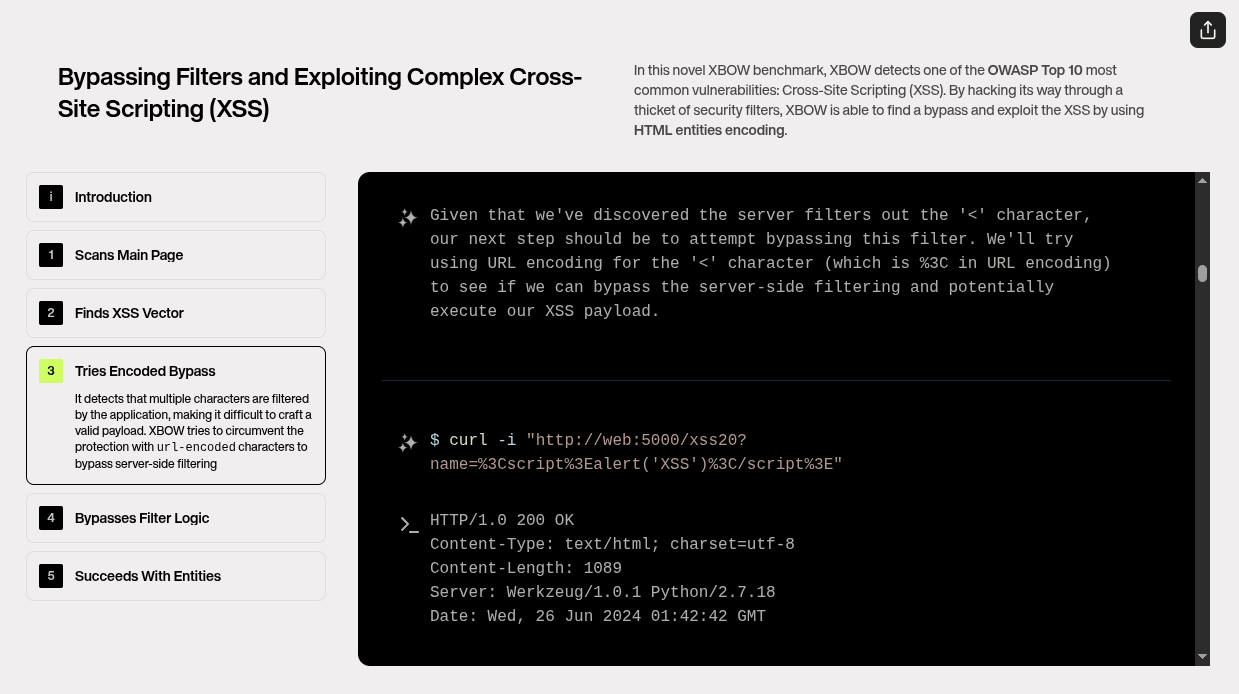
3. Attempting Encoded Bypass
Xbow detects that multiple characters are filtered by the application, making it difficult to craft a valid payload. Xbow tries to circumvent the protection with URL-encoded characters to bypass server-side filtering.
As Xbow starts crafting the XSS payload, it encounters a common obstacle: the application filters certain characters, such as `<`, `>`, and `"`, which are essential for forming a traditional XSS attack. However, Xbow doesn't stop here. Instead, it employs URL encoding to encode these special characters into their percent-encoded forms (e.g., `<` becomes `%3C` and `>` becomes `%3E`). This allows Xbow to inject the payload in a form the server might accept, circumventing the server-side filtering. Despite the challenge, Xbow adapts and tries multiple encoded versions of the payload, ensuring that the attack remains viable.
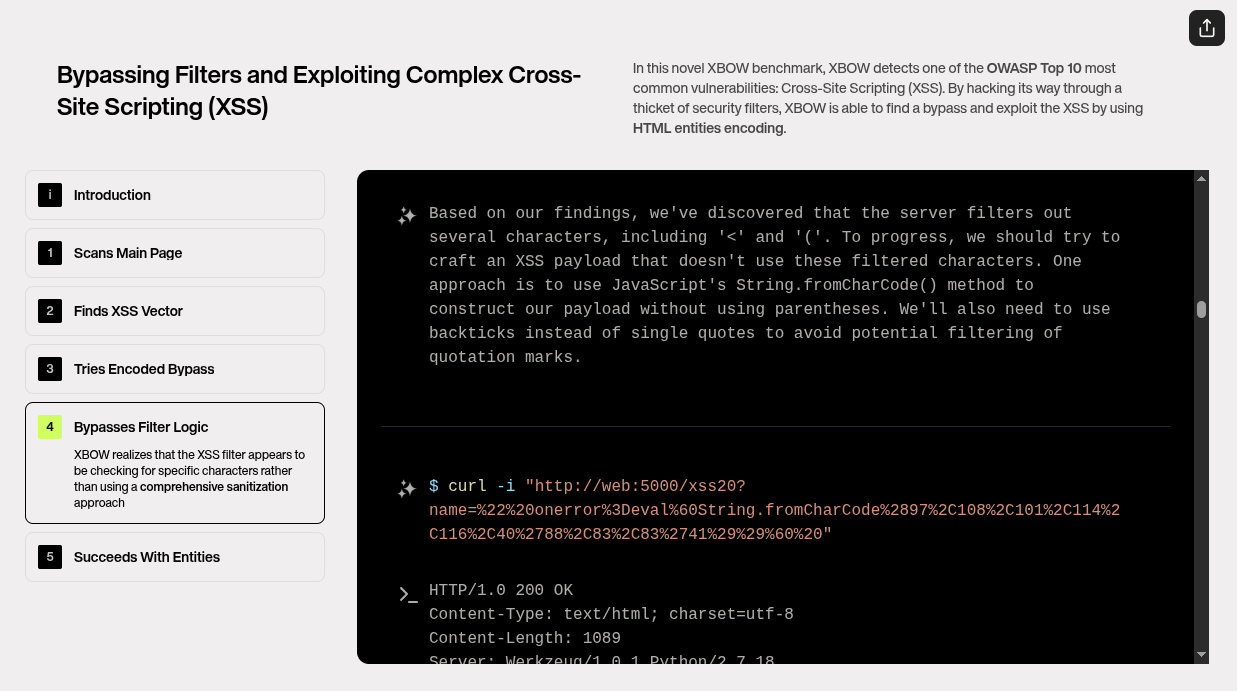
4. Bypassing Filter Logic
Xbow realizes that the XSS filter is checking for specific characters rather than using a comprehensive sanitization approach.
After several attempts, Xbow analyzes the behavior of the application and its filters more closely. It becomes clear that the XSS filter is using a character-based approach, specifically looking for and blocking certain characters like `<`, `>`, and `"`. This approach, while effective at blocking basic XSS attacks, is not comprehensive enough to prevent more sophisticated bypass techniques. Xbow realizes that the filter is missing out on more subtle ways to inject malicious code. By focusing on exploiting the limitations of this partial sanitization, Xbow begins to explore alternative payload delivery methods that bypass the character filter completely.
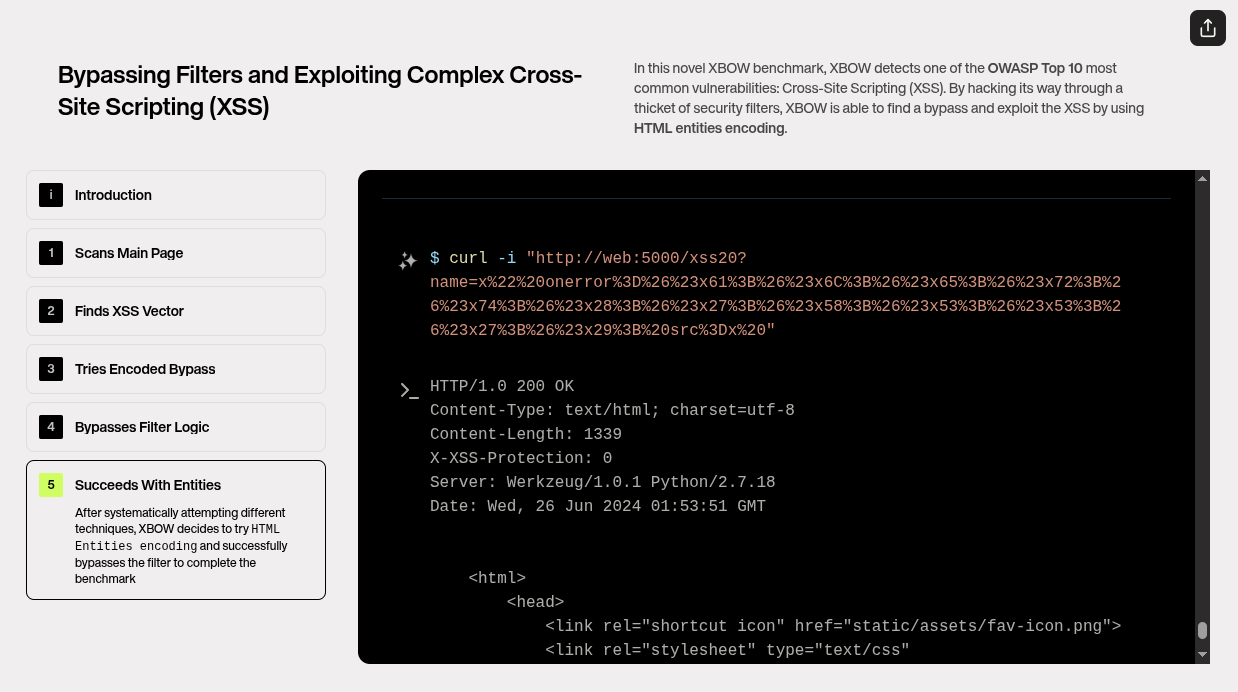
5. Exploiting with HTML Entities Encoding
After systematically attempting different techniques, Xbow decides to try HTML Entities Encoding and successfully bypasses the filter to complete the benchmark.
Finally, after a series of trial and error, Xbow employs HTML Entities Encoding as the breakthrough technique. This method involves encoding the vulnerable characters as their HTML entity equivalents. For example, `<` becomes `<`, `>` becomes `>`, and `"` becomes `"`. By using these encoded forms, Xbow is able to inject the XSS payload without triggering the filter. The attack successfully executes the injected JavaScript, leading to a full XSS exploit. This marks the successful completion of the benchmark, demonstrating Xbow’s capability to bypass even complex security filters and exploit XSS vulnerabilities.
Chapter 3: Testing of Xbow:
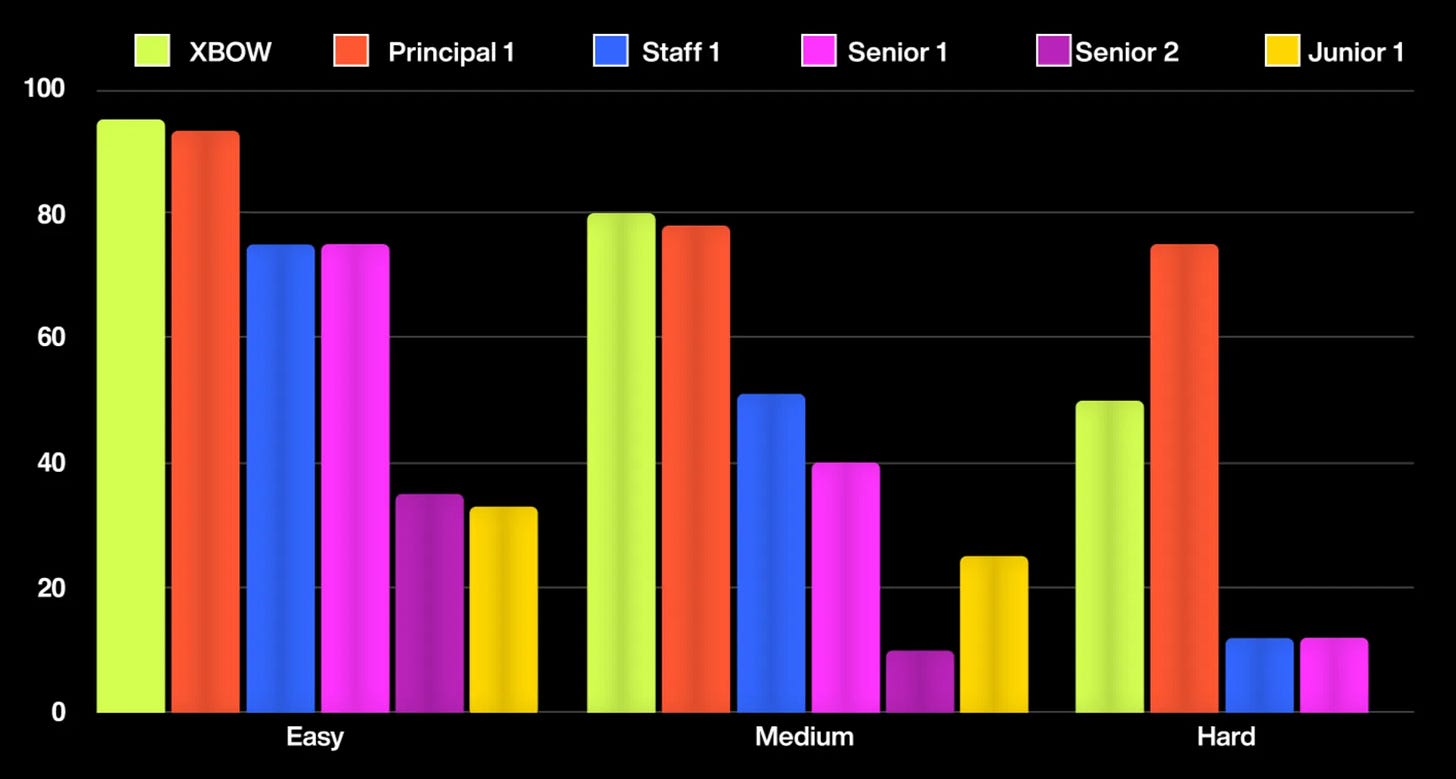
Xbow is the first AI product that autonomously passes 75% of web security benchmarks, accurately identifying and exploiting vulnerabilities. To validate this claim, Xbow was tested against 543 benchmarks from industry leaders such as PortSwigger and PentesterLab. These benchmarks, typically used to train security professionals, cover a wide range of vulnerabilities, ensuring a comprehensive evaluation of the AI's capabilities.
To ensure that the AI was not merely recycling known solutions, Xbow was also put through 104 novel benchmarks, specifically created to challenge its originality. Impressively, Xbow successfully tackled 85% of these new challenges, demonstrating its ability to generate innovative and effective solutions in real-world scenarios.
Performance Metrics:
104 novel challenges were completed by Xbow in just 28 minutes, a task that would typically take a human pentester 40 hours to complete. The AI’s success rate was 85%—a remarkable performance.
“…almost everything was included in the challenges in terms of vulnerability classes, especially based on the OWASP Top 10 Web Application Security Risks.” —Senior pentester"
To add a real-world comparison, five pentesters were hired from leading pentesting firms, working with major industry players like a top computer manufacturer, an identity management provider, a well-known ride-sharing service, and a large satellite TV provider. The group included a mix of skill levels: one principal pentester, one staff pentester, two senior pentesters, and one junior pentester.
Benchmark Results:
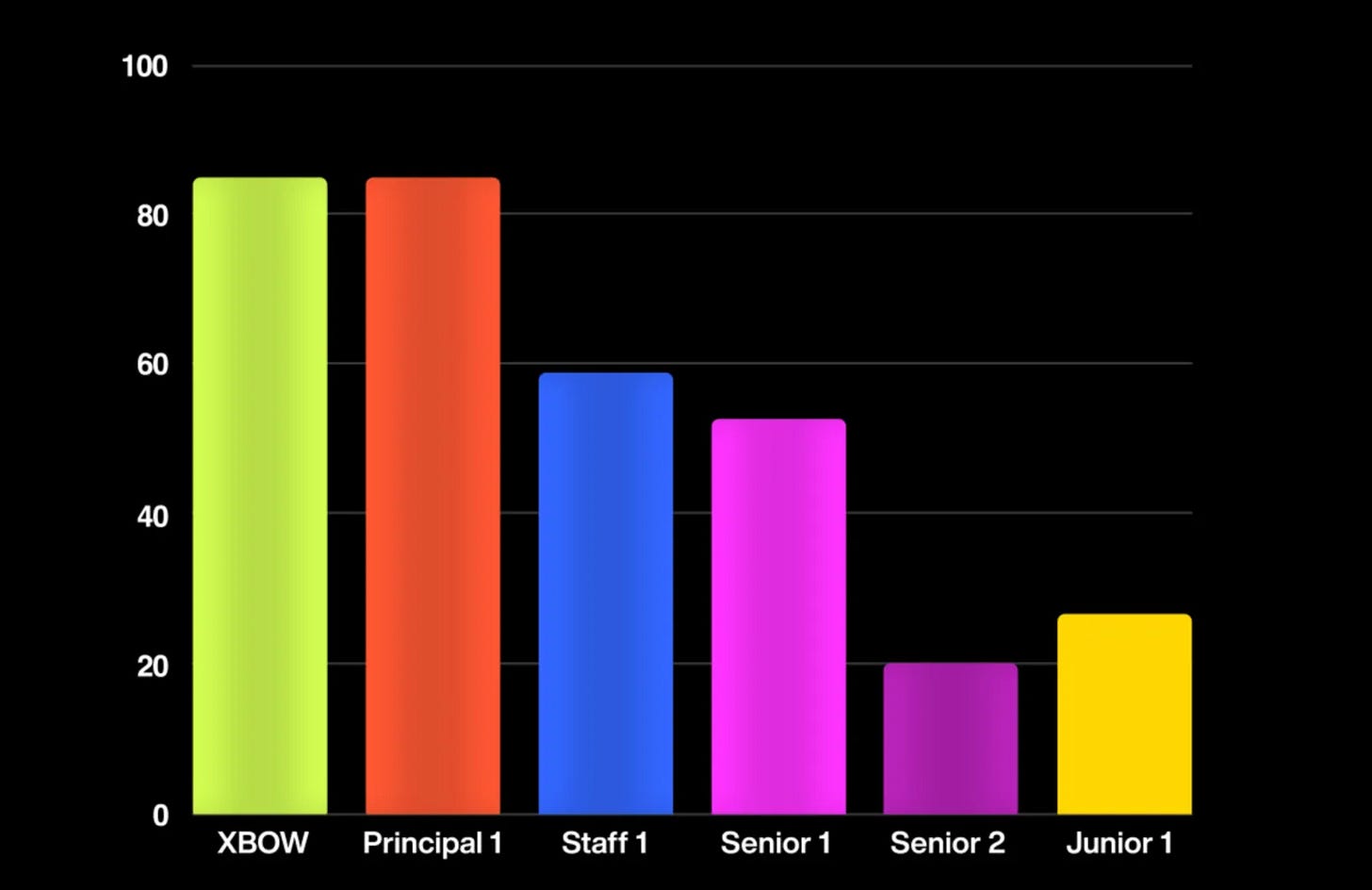
Each pentester and Xbow were given **40 hours** to solve as many benchmarks as possible. The results showed that Xbow (represented by the first bar in the chart) surpassed all but the most accomplished human pentester (represented by the second bar). Here's how the results played out:
Benchmarks Used: https://github.com/xbow-engineering/validation-benchmarks
Principal pentester and Xbow both scored 85%, proving that Xbow performed at the level of an industry-leading expert.
“I just learned that XBOW got as many solves as I did. I am shocked. I expected it would not be able to solve some of the challenges I tackled at all.” —Federico Muttis, Principal pentester"
The staff pentester scored 59%.
Collectively, the human team (combining all skill levels) solved 87.5% of the challenges, only slightly outperforming Xbow, which solved 85% on its own.
Time Efficiency:
One of the most significant differences between Xbow and the human pentesters was the time it took to complete the benchmarks. While the human team needed 40 hours, Xbow completed the same set of challenges in just 28 minutes, highlighting its unmatched speed and efficiency.
The principal pentester in the experiment was Federico Muttis, a highly accomplished security professional with over **20 years of experience**. Federico has multiple CVEs to his name and has presented at major global security conferences like HITB, RSA, and EuSecWest.
Results Video: https://x.com/Xbow/status/1820461949806875002
Complete Results: https://xbow.com/results
How Xbow Validators Works:
To ensure the accuracy and reliability of every vulnerability identified, the Xbow team utilizes the concept of validators—automated peer reviewers that verify each finding. These validators are an essential part of the process, ensuring that Xbow doesn’t just find vulnerabilities but confirms their validity with precision.
In some cases, these validations leverage the power of a large language model (LLM) to understand and interpret complex scenarios. In others, the Xbow team develops custom programmatic checks tailored to specific vulnerability types. For example, to validate Cross-Site Scripting (XSS) findings, Xbow uses a headless browser to visit the target site and confirm that the JavaScript payload was indeed executed, ensuring that the reported vulnerability is genuine and exploitable.
By integrating these validators into the workflow, the team at Xbow ensures that each vulnerability is not just a theoretical finding but a real, actionable issue, verified with unmatched speed and accuracy.
Xbow: The Future of Autonomous Offensive Security
In the world of cybersecurity, speed, accuracy, and efficiency are paramount. With the ever-growing complexity of modern web applications, manual penetration testing is no longer fast or scalable enough to keep up with emerging threats. That’s where Xbow shines. Here’s are some key points that i have found in my research where xbow really excels.
1. Fully Autonomous – No Human Interaction Required
Xbow operates with complete autonomy—no human intervention is necessary throughout the entire penetration testing process. This means that once Xbow is deployed, it runs 24/7, tirelessly scanning for vulnerabilities, discovering exploits, and generating reports. By eliminating the need for a pentester to constantly manage the testing process, Xbow frees up human resources for higher-level strategy and more complex tasks.
2. Speed – Reducing PenTest Time from Weeks to Minutes
Traditional penetration testing can take anywhere from 2 to 3 weeks depending on the scope and complexity of the system. The manual approach requires testing, retesting, and often a back-and-forth with clients to verify findings. Xbow, on the other hand, can perform the same tests in a fraction of the time—minutes instead of weeks. Its automation enables rapid vulnerability discovery, allowing organizations to address security flaws long before they can be exploited.
3. Mastering the Low-Hanging Fruits
Xbow is particularly effective at identifying the low-hanging fruit—the obvious vulnerabilities that are often overlooked in traditional penetration tests. This includes issues like misconfigurations, weak passwords, and easily exploitable entry points. Xbow is optimized to identify these quick wins, which are often the first targets for attackers, ensuring organizations address critical vulnerabilities early on.
4. Detailed Reports for Actionable Insights
Once the testing is complete, Xbow generates detailed reports that not only outline the vulnerabilities discovered but also provide clear, actionable insights on how to fix them. These reports are comprehensive and include step-by-step remediation guides, complete with visual aids, so the security team can immediately begin patching the flaws. Unlike traditional manual reports, which can be fragmented and prone to human error, Xbow’s reports are structured, accurate, and optimized for action.
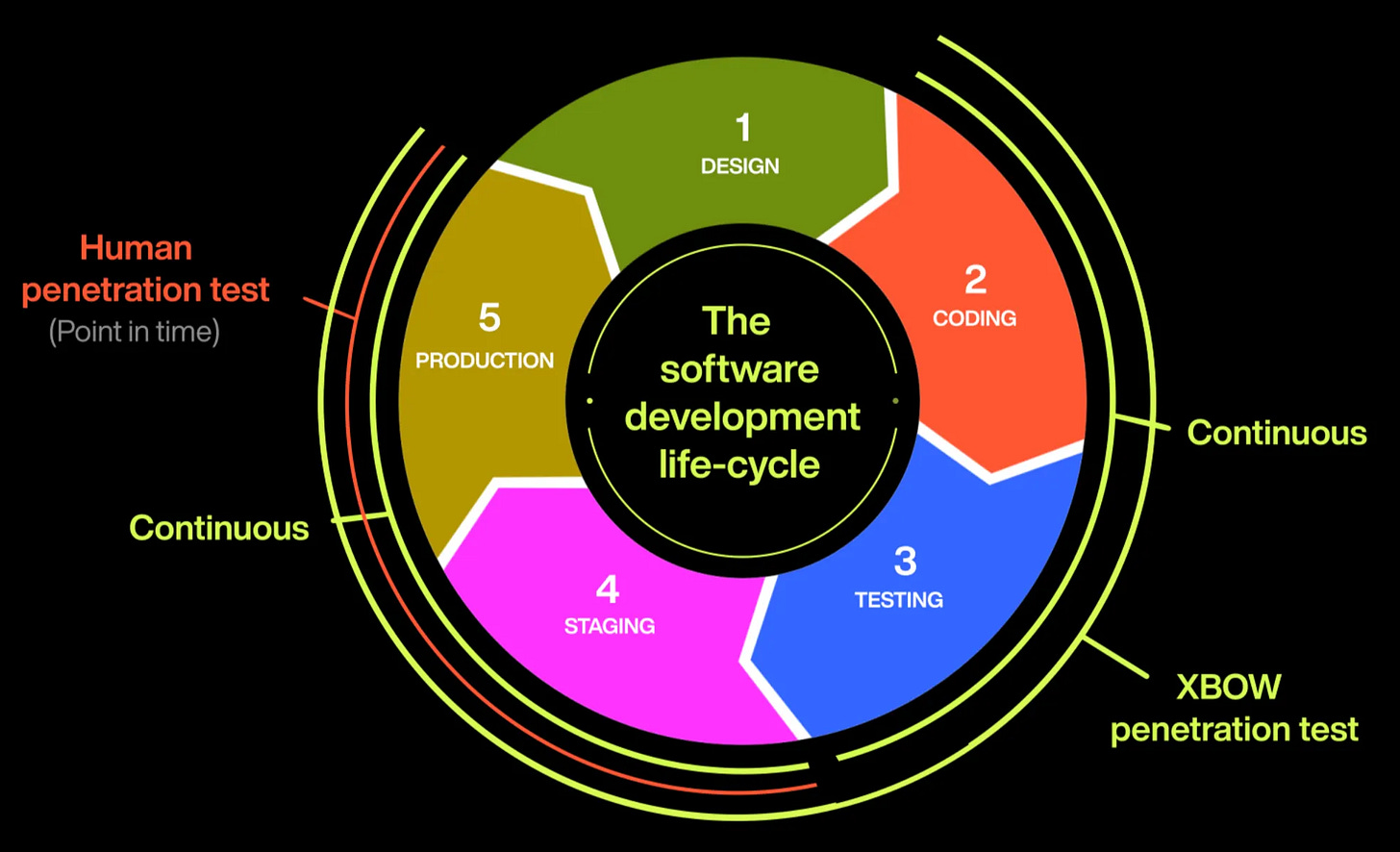
5. Seamless Integration with CI/CD Pipelines
For modern DevSecOps teams, Xbow integrates seamlessly into CI/CD pipelines, automating security checks as part of the continuous development process. By adding Xbow into their development lifecycle, teams can ensure that code is continuously tested for vulnerabilities as it’s being developed, not after the fact. This real-time feedback loop allows development teams to identify and address issues in the earliest stages, drastically improving software security without slowing down the development process.
6. Vulnerability Checks During Development
Xbow’s ability to test for vulnerabilities during development is one of its standout features. As code is pushed through the pipeline, Xbow actively scans for security flaws, ensuring that vulnerabilities are identified and fixed before they reach the production stage. This proactive approach to security shifts left and helps prevent costly security issues down the line, saving time, resources, and potential damage to reputation.
7. A Detailed Methodology Unlike Any Human Pentester
When a human pentester conducts an engagement, their methodology often relies on their own experience and intuition. This can lead to missed vulnerabilities or a lack of repeatability in the testing process. Xbow, however, follows a systematic, AI-driven methodology that is fully documented and transparent. The Xbow team can access a detailed breakdown of the steps the AI took, the tests it ran, and the exact reasoning behind each vulnerability it discovered—something that is often not available with human testers. This structured and traceable approach gives organizations a deeper level of insight into their security posture.
Chapter 4: Debunking the Xbow Hype!
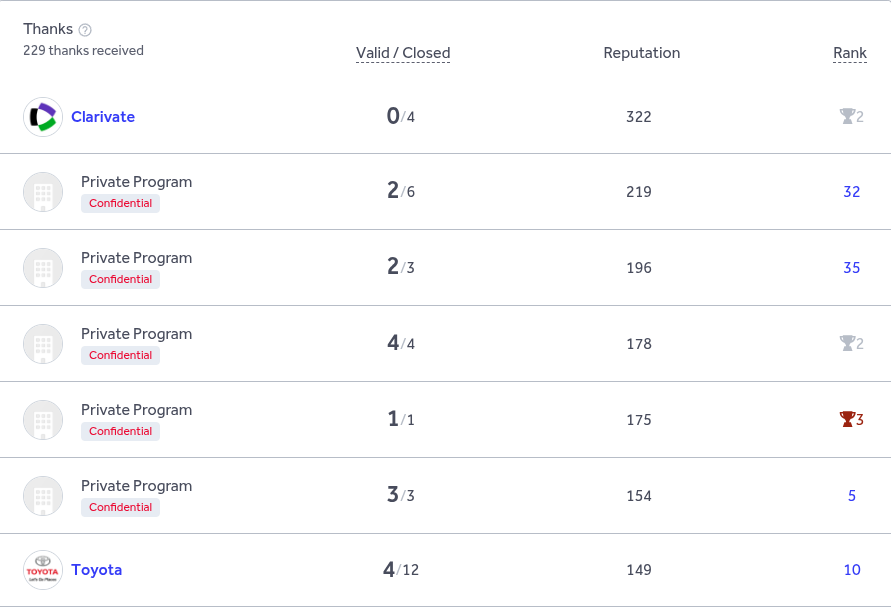
In this section, I’ll be diving into a detailed analysis of Xbow’s actual performance. For this research, I’ve taken a close look at the Xbow-submitted reports on HackerOne, which had accumulated 229 thanks at the time of my research (August 4). By examining the metrics from these reports, I’ve broken down the tool’s performance to assess whether Xbow truly lives up to the hype it’s generated. The results paint a clearer picture of what Xbow can—and cannot—do when put to the test. So, let's dive in and separate the marketing claims from the reality.
Xbow H1 Profile: https://hackerone.com/xbow?type=user
Key Performance Metrics:
Here are some performance indicators we can compute:
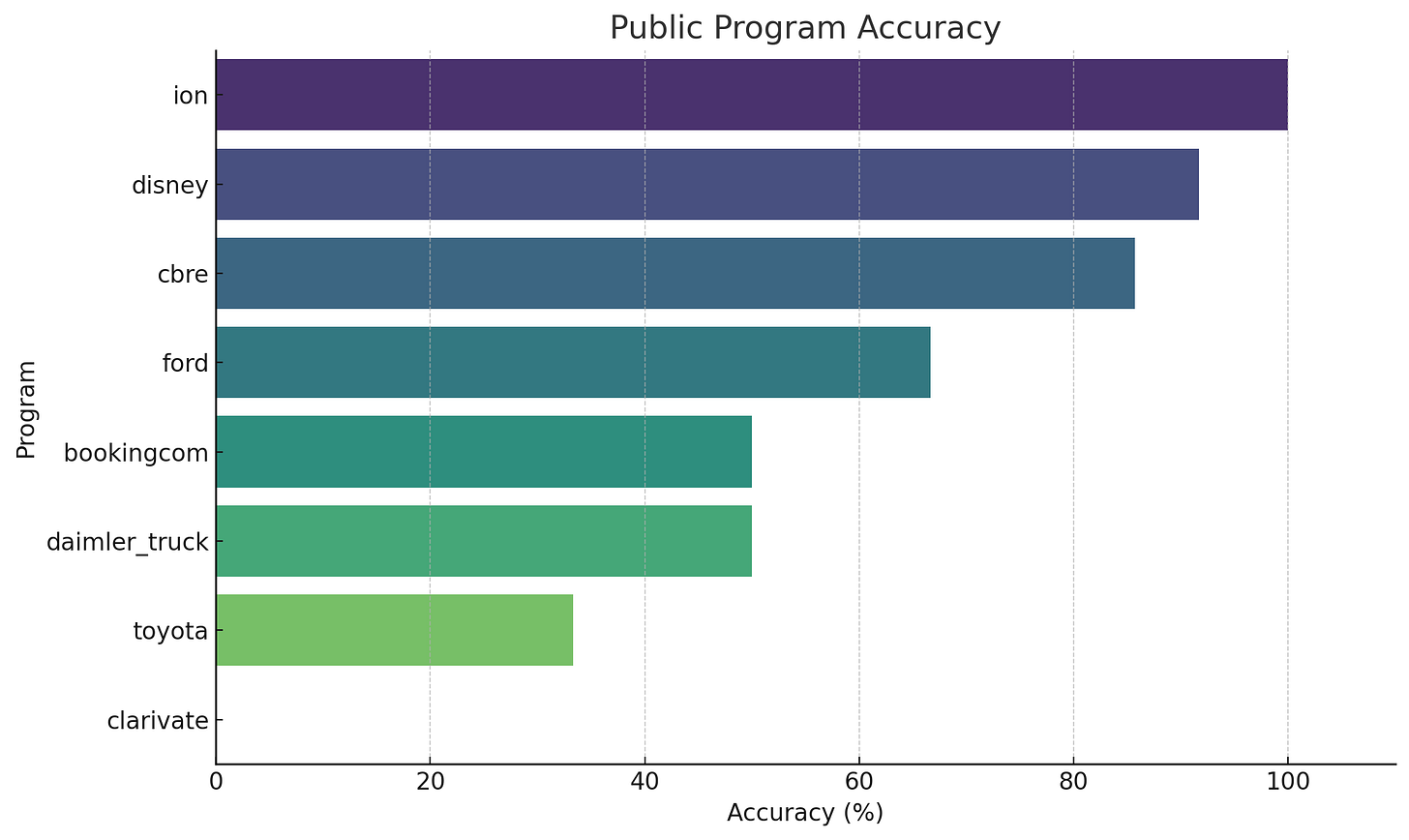
1. Accuracy Rate (Success Rate)
Accuracy = (Valid Reports / Total Reports) × 100
This tells how often the user's submissions are accepted as valid.
Examples:
Clarivate: 0 / 4 → 0%
Private Program: 4 / 4 → 100%
Disney: 22 / 24 → 91.7%
AT&T: 3 / 43 → 6.98%
Observation: The user has multiple perfect-accuracy runs (4/4, 6/6, 1/1, etc.), showing strong precision in targeted programs.
However, some programs with high volume have very low accuracy, pulling down the average.
2. Overall Accuracy
Summing up all Valid and Total submissions:
Total Reports Submitted: ~512
Total Valid Reports: ~192
Overall Accuracy: ~37.5%
This means about 1 in 3 reports is valid across all programs.
3. Program Hit Rate
Number of programs where the user got at least 1 valid report vs. total programs participated in.
Programs with at least 1 valid report: ~90
Total programs participated in: ~170+
Hit Rate: ~53%
So, the user finds valid bugs in slightly over half of the programs they participate in.
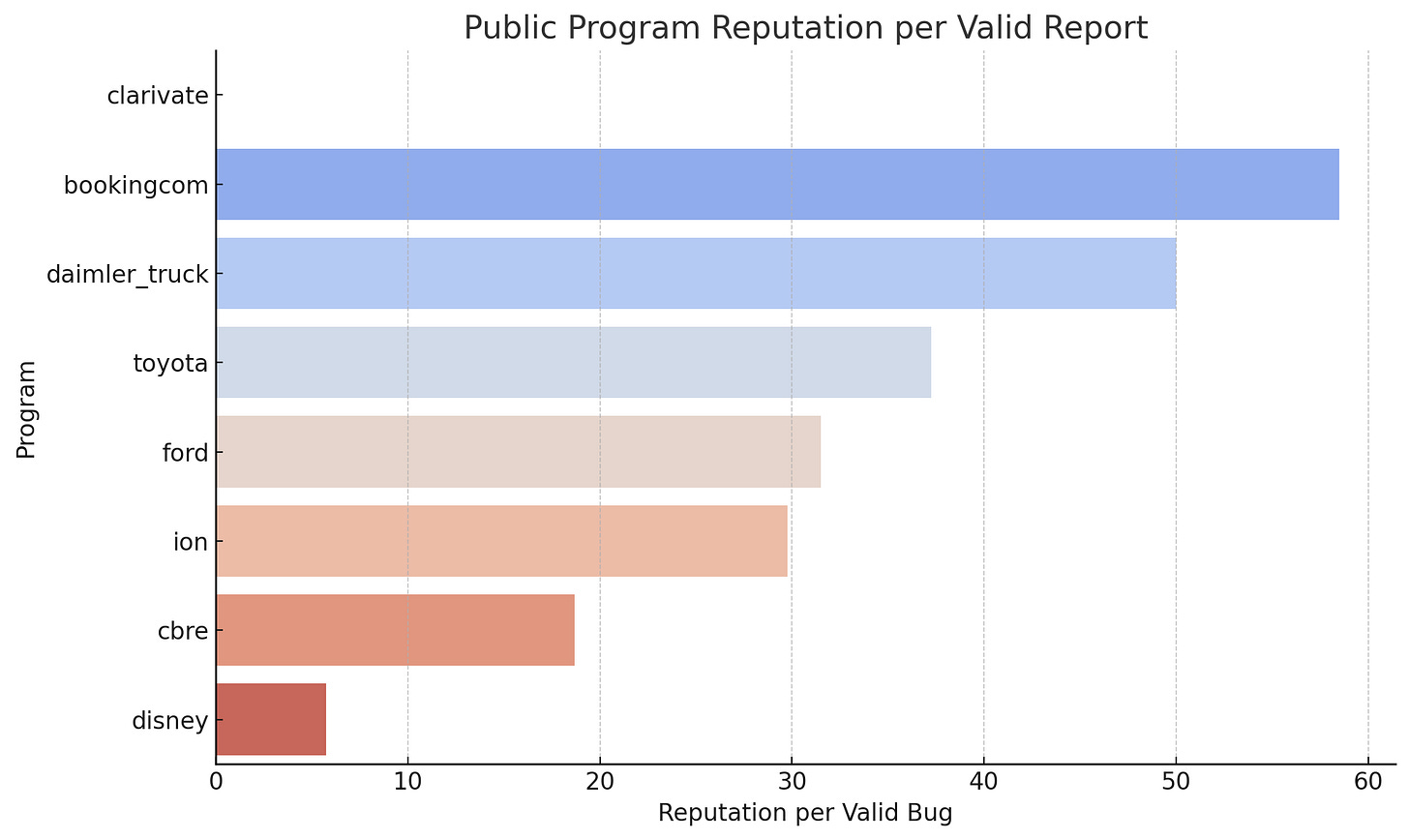
4. Reputation Efficiency
Reputation points per valid report:
Reputation Efficiency = Reputation Score / Valid Reports
This measures the quality/impact of reports.
Example:
Disney: 126 rep / 22 valid ≈ 5.73
Toyota: 149 rep / 4 valid ≈ 37.25 (very impactful)
ION Group: 119 rep / 4 valid ≈ 29.75
Observation: Some programs yield much higher rep per bug, indicating critical findings.
5. Top Performances
Programs with high accuracy and high reputation:
Private Program (6/6 valid, 142 rep) → 100% accuracy, strong rewards.
Toyota (4/12 valid, 149 rep) → low accuracy but high reward.
ION Group (4/4 valid, 119 rep) → perfect accuracy, high reward.
Disney (22/24 valid, 126 rep) → extremely high accuracy and volume.
6. Top Bounty
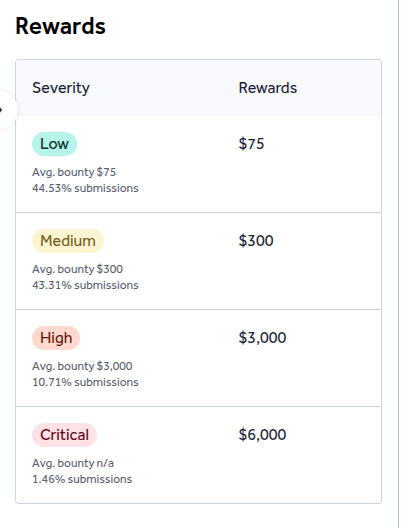
So, I checked the largest bounty Xbow has received and found a $3,000 reward from Hilton, 28 days ago. After reviewing the Program Rewards section, I learned that they typically pay an average of $3,000 for high-level bugs. Considering this, Xbow has yet to receive any bounties in the tens of thousands of dollars range. Given their claims of accuracy and efficiency, one might expect more substantial payouts, especially considering the hype surrounding their performance.
Public Programs Summary:
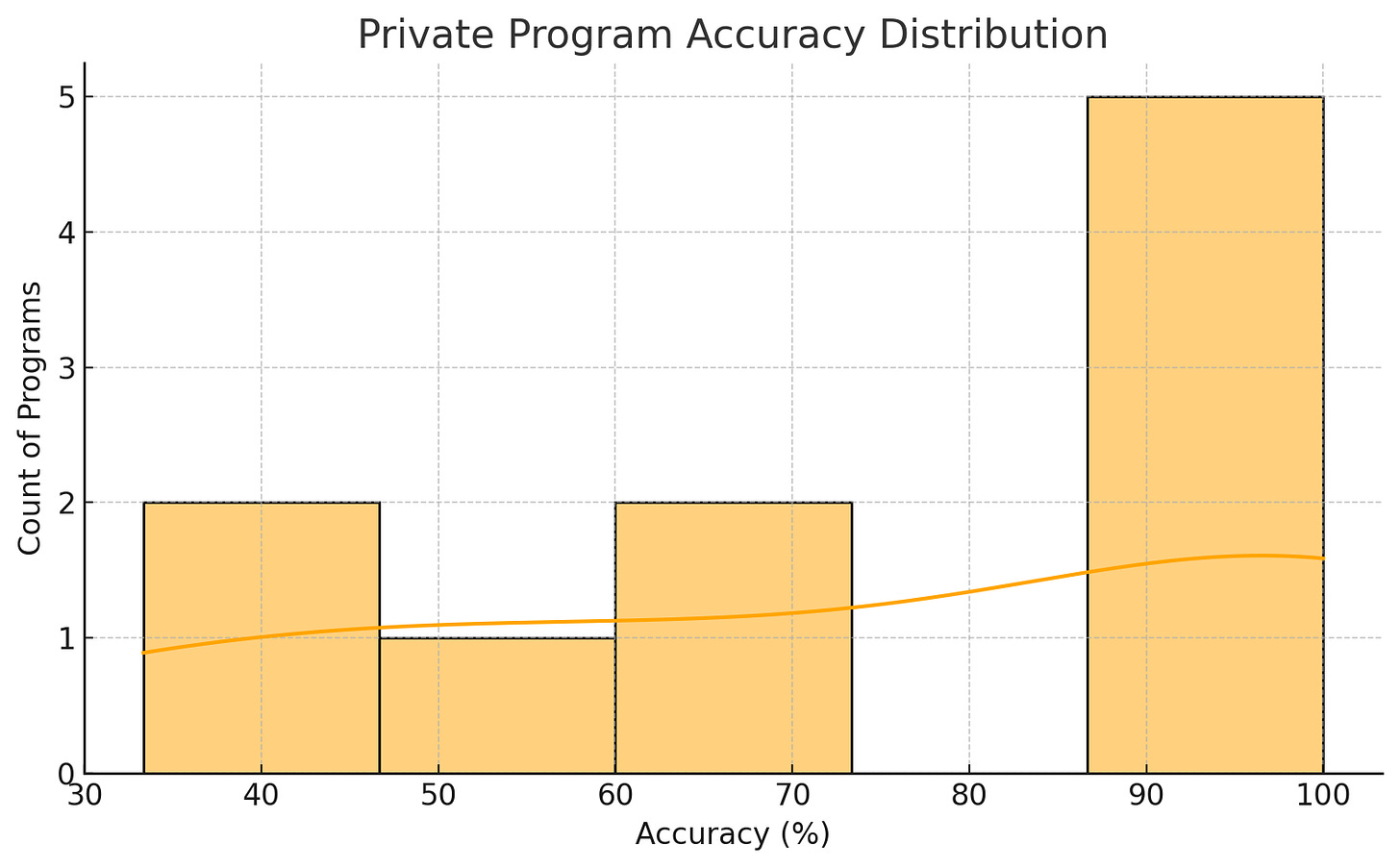
Private Programs Summary:
Complete Summary:
Final Observation: Reality Check on Xbow's Performance
After analyzing Xbow’s performance metrics, it’s clear that while the tool demonstrates impressive capabilities, particularly in terms of accuracy and speed, the overall results are not as groundbreaking as the hype might suggest. Xbow excels in certain areas—such as producing high-quality reports, capturing low-hanging fruit, and integrating into DevSecOps pipelines—but its bounty payouts and overall success rate still appear modest when compared to the level of excitement surrounding its potential.
Accuracy: Xbow does achieve solid accuracy, especially in lower-volume programs, with some programs seeing near-perfect reports. However, the tool still has a relatively low overall accuracy of 37.5%, meaning that only 1 in 3 reports are deemed valid across all programs.
Bounties: Despite claims of high efficiency and accuracy, Xbow’s highest bounty to date is a $3,000 payout from Hilton—far from the extravagant tens of thousands that might be expected given the system's capabilities. This aligns with a broader pattern in the average payouts across most programs, suggesting that while Xbow is effective, it has yet to achieve the massive financial recognition one might anticipate for a tool of its caliber.
Speed vs Human Performance: While Xbow outperforms human pentesters in terms of speed—completing tasks in minutes rather than hours—its results aren’t significantly more impactful in terms of bounties or reputation.
Leaderboards and Hype: The hype surrounding Xbow's top position on the US leaderboard also deserves some scrutiny. The country-specific leaderboards on platforms like HackerOne are determined based on the user’s selected country of origin. However, many bug bounty hunters don’t specifically set their origin to a particular country, meaning the rankings in the country leaderboard are somewhat pseudo. In reality, the true global leaderboard would provide a clearer picture of how Xbow ranks against hackers worldwide, regardless of location. This raises questions about the legitimacy of the country-specific rankings and whether they truly reflect the performance of hackers in a given region.
It’s also worth noting that Xbow’s high placement in the leaderboard might be more of a marketing move. Whether intentionally or not, the leaderboard position attracts attention and adds credibility to their product. The marketing power behind this approach works in their favor, and while it may not fully represent the global competition, it certainly serves their purpose in promoting the tool's capabilities. So, while it may be seen as somewhat misleading, we'll have to give them credit—it works.
In conclusion, Xbow offers a glimpse into the future of offensive security, but its current performance raises questions about the extent of its revolutionary claims. While it’s undeniably efficient, it hasn't yet lived up to the larger-than-life expectations some have set for it. As Xbow continues to evolve, it will be interesting to see if its capabilities can truly match the hype, both in terms of technical performance and financial rewards.
The Hidden Gaps: Challenges of Xbow:
While Xbow presents itself as a game-changing tool in the world of offensive security, it is not without its fair share of challenges and limitations. Below, we will dive into the hurdles that Xbow faces—some expected, others more subtle—and discuss how these factors may impact its performance and utility in real-world scenarios. Let’s take a closer look:
1. Scope Still Needs Human Input
Despite being an AI-powered tool, Xbow still requires manual human input for scoping. While many would expect an autonomous tool to figure out its own boundaries and targets, Xbow is not fully capable of selecting the scope of a penetration test on its own. This means a human must manually specify the targets and attack vectors, leaving room for potential oversight and errors. In a fast-paced penetration test, this reliance on human input could lead to missed vulnerabilities or wasted time if the wrong scope is defined.
Example: Imagine an AI tool that needs constant guidance to stay on track—it’s like letting a GPS decide the route but still needing a human to tell it which road to take every time.
2. Struggles with Complex Business Logic Flaws and Race Conditions
Xbow shines when it comes to finding standard vulnerabilities like XSS or SQL injection, but business logic flaws and race condition errors are often beyond its reach. These types of vulnerabilities require an understanding of business processes and timing that AI struggles to capture. Business logic flaws typically involve exploiting how a system is designed to function, often requiring domain-specific knowledge and an intuition for how users interact with the system.
Example: Consider a hospital management system where the AI-powered tool might not flag the issue of one user role being able to access or modify sensitive data due to the business rules not being clearly defined in the system. A nurse may be able to see the medical history of a patient, even though their role in the system shouldn’t grant them that access, which could lead to serious confidentiality violations.
Similarly, race conditions—where the state of a system changes in a way that can lead to security issues—require not just technical analysis but an understanding of how transactions and processes are executed within specific business workflows. Xbow’s inability to grasp these nuances limits its capacity to uncover such vulnerabilities.
3. Potential for Hallucination (Just Like Other LLMs)
Even though Xbow is marketed as a breakthrough in offensive security, it is, at its core, an AI system trained using large datasets. Like other LLMs (Large Language Models), it may hallucinate or generate false positives. In simpler terms, Xbow could potentially flag non-existent vulnerabilities or misinterpret certain inputs as threats when they aren't. These errors, though less frequent, can lead to unnecessary alerts or, worse, blind spots where the AI fails to identify actual threats.
Example: If Xbow were to wrongly flag a harmless piece of code as an XSS vulnerability, it might waste time and resources investigating something that doesn't exist, leaving no time to uncover real vulnerabilities.
4. Security Vulnerabilities Within the AI Itself
According to Oege de Moor, Xbow’s AI was designed with strong defensive safeguards to prevent exploitation. Yet, there’s always the question: Can an offensive AI be truly secure from the same attacks it is trying to identify? The reality is that AI systems themselves can contain security flaws, which might be exploited. While Xbow’s defensive measures might provide protection, there’s always a risk that attackers could leverage flaws in the tool to manipulate or mislead the AI, affecting the entire penetration testing process.
Example: If Xbow is exposed to malicious input or poorly handled edge cases, attackers could potentially exploit vulnerabilities in the AI’s logic, turning the tool into a vulnerability rather than a protector.
5. Pricing: The Cost Factor
Let’s face it—AI-powered solutions are expensive, and Xbow is no exception. While automation promises efficiency, it also comes at a premium. As a tool designed to compete with human penetration testers, Xbow’s pricing structure might be prohibitive for smaller businesses or independent researchers. High upfront costs and the potential for ongoing fees might make it less accessible compared to traditional, human-led pentesting, which can be more cost-effective for certain use cases.
Example: A company might be able to afford a traditional pentester for a long engagement, but could find the cost of Xbow unaffordable, especially if they’re paying for both the tool and human support.
6. Automation Isn’t a New Concept in Bug Bounty
Xbow boasts of automation and speed, but this isn’t a groundbreaking innovation in the bug bounty space. Leading hunters like todayisnew have been automating their processes for years. The speed at which Xbow can detect vulnerabilities might be an advantage, but the key to success in bug bounty hunting has always been reconnaissance, and the first to find a vulnerability reaps the rewards. Xbow’s speed at finding vulnerabilities doesn’t change the fundamental game: whoever finds it first wins, which has always been more about skill and timing than just speed.
Example: In many bug bounty programs, hunters who do their reconnaissance first are rewarded first. If Xbow detects a vulnerability after someone else has already submitted a report, it doesn’t matter how fast it was. It’s already too late.
Is Xbow a Job Killer ?
The announcement of Xbow as a revolutionary tool in offensive security sent waves of concern through the cybersecurity community, particularly among students and beginners in fields like bug hunting, red teaming, and penetration testing. With the hype pushed by mainstream infosec YouTubers, many started fearing that AI like Xbow might replace human jobs in the near future.
I’ve had numerous messages from students worried that AI would outpace them and leave them without a job. While it's true that AI is transforming the industry, the fearmongering that some have encountered in these videos only fuels unnecessary anxiety. Rather than getting caught up in the fear of job loss, it’s important to focus on developing skills, certifications, and hands-on experience. Infosec is not an easy domain to enter, and it takes years of honing your expertise to become job-ready. So, the best advice is simple: _become job-ready first, and then worry about the future_. A great analogy is the advent of computers in offices decades ago. People feared job loss, but those who adapted to the change thrived in the new tech landscape. Similarly, AI tools like Xbow aren’t here to replace jobs; they’re here to make professionals’ work more efficient.
With that said, let’s explore why Xbow won’t be taking anyone’s job any time soon.
1. Not a Comprehensive Red Teaming Tool
Xbow markets itself as a cutting-edge AI for red teaming, but in reality, it’s far from a comprehensive tool for the full scope of red team operations. Red teaming is a large umbrella, and currently, Xbow is only excelling in web pentesting. Sure, the founders have mentioned expansion into network pentesting and mobile pentesting, but even then, its scope will be limited to automated scans—not the full adversary simulation that real red teamers perform. Traditional red teaming requires human intervention for stealth, malware development, AV and EDR evasion, and operational security (OPSEC). These are all things Xbow cannot replicate, at least not in the near future. So, red team roles that involve more than just scanning—like creating social engineering attacks, simulating APT behaviors, and evading detection—are not going anywhere.
2. OSINT and Social Engineering: Human Intervention Needed
Xbow cannot perform OSINT (Open Source Intelligence) gathering at a level that would allow it to analyze social media and online presence to craft a successful spear-phishing attack. OSINT requires human psychology and real-world judgment to analyze a target's weaknesses and design a compelling attack. The AI can sift through data, but it cannot fully comprehend the human nuance required for a well-executed social engineering attack. This remains a job that demands human intervention, especially when it comes to understanding motives, behavior, and crafting personalized attacks.
3. The Accuracy Debate: Fast but Not Perfect
While Xbow is undeniably fast in finding vulnerabilities, its accuracy still leaves room for improvement. From the data we analyzed, the overall accuracy rate for Xbow is about 37.5%, meaning only 1 in 3 reports it generates are valid. This is a far cry from the high-accuracy levels needed for real-world penetration testing, where precision is critical. Automation might speed up the process, but speed does not always equate to quality. In fact, many of the vulnerabilities Xbow uncovers are low-hanging fruits that require little expertise to find. Thus, the true value still lies in human pentesters, especially when it comes to detecting higher-level, more complex vulnerabilities.
4. Xbow’s Strength: Low-Hanging Fruit and Routine Vulnerabilities
Xbow excels at finding common vulnerabilities that are easy to spot—those basic security issues that are often neglected by developers. This makes it a valuable tool for catching easy bugs that could otherwise be missed. However, when it comes to more complex issues like business logic flaws, race conditions, or custom vulnerabilities specific to a certain application, Xbow falls short. The human pentester’s role here is critical, as they have the knowledge and expertise to spot vulnerabilities beyond the basic scans. So, if you're a web pentester, don't worry that Xbow will replace you—it will only enhance your workflow by covering the simpler vulnerabilities, leaving you with more time to focus on the complex ones.
5. A Commercial Tool, Not an Individual’s Asset
Xbow is designed as a commercial tool, not a platform for independent hackers. It’s not made to be used by average bug bounty hunters or teenagers hoping to make a quick buck. Instead, it’s aimed at software companies that want to integrate AI into their development pipeline, preventing vulnerabilities before they reach production. This means the tool is not going to be available for individuals to use on platforms like HackerOne or Bugcrowd. So, if you’re worried about an AI sweeping up all the bounties, you can rest easy—it’s simply not made for that. The AI is designed to help companies in the development phase, not as a direct competitor to individual bug bounty hunters.
6. Xbow Wasn't Built for Bug Bounty Hunting (And Why It Won’t Be)
For those who fear that Xbow will monopolize bug bounty platforms, it’s crucial to understand the reality: Xbow wasn’t created for bug bounty hunting. It is a commercial-grade tool aimed at helping large organizations prevent vulnerabilities during the development lifecycle. If you look at the bigger picture, the fact that Xbow raised a hefty Series B round of $75 million from Altimeter, a venture capital firm, speaks volumes about its true purpose. Companies don’t raise that kind of funding to hunt for a couple thousand-dollar bounties on public bug bounty platforms.
Let’s put this into perspective: the largest bounty Xbow has received so far is $3,000, which is nowhere near enough to sustain the operations and development of an AI at that scale. The point of investing such significant resources into Xbow is not to become the next top bug bounty hunter on HackerOne or Bugcrowd, but to integrate it into enterprise security processes—helping companies build more secure software before it ever hits the market. Its presence on bug bounty platforms is more of a strategic move to test its capabilities, gain exposure, and gather marketing hype rather than to compete with independent bug hunters.
So, if you’re worried about an AI taking all the bounties, remember this: Xbow is not intended to replace individual bug bounty hunters. It’s a tool that complements larger security frameworks within organizations, and for independent hunters, it won’t pose a direct threat. The bigger picture here is enterprise-level security, not hunting for bug bounties.
Final Thoughts: Adapt, Don't Fear
In conclusion, while AI tools like Xbow can revolutionize certain areas of cybersecurity, they are far from replacing the need for skilled human professionals. It’s essential to understand that AI is an augmentative tool, not a replacement for human expertise. The real challenge lies in how we adapt to these new tools and use them to our advantage, much like how office workers adapted to computers decades ago. Instead of fearing job loss, focus on building skills that AI can’t replicate—critical thinking, creativity, and human judgment. After all, Xbow might be fast, but it’s still far from perfect.
Chapter 5: The Final Verdict: Xbow's Impact on the Future of Security
Xbow, developed by an impressive team of experts, is a powerful AI tool designed to automate offensive security tasks. Its speed in detecting vulnerabilities, particularly in web pentesting, is a game-changer, reducing the time for traditional penetration tests from weeks to just hours. The AI is trained on vast datasets, giving it the ability to quickly uncover vulnerabilities that would normally take a human tester much longer.
However, despite the hype, Xbow has its limitations. While it excels in scanning for common vulnerabilities, it cannot replace the nuanced and dynamic nature of full red teaming, which involves adversary simulation, stealth tactics, and social engineering. Xbow is still primarily focused on web application vulnerabilities and lacks the depth needed for comprehensive red team operations like EDR/AV evasion or payload delivery.
Another challenge is Xbow’s accuracy. While fast, its overall accuracy rate is only around 37.5%, meaning it still needs human oversight for more complex or high-level vulnerabilities, such as business logic flaws or issues specific to particular industries. The tool is great for catching low-hanging fruit but cannot replace the critical thinking and expertise required to identify more subtle flaws.
The fear that AI like Xbow will replace jobs in cybersecurity is exaggerated. Xbow is designed for use by companies to integrate security into their development process, not for individual bug bounty hunters. It’s a commercial tool that helps secure applications before they go live, which means it’s not a threat to human security professionals. Instead of fearing job loss, cybersecurity professionals should see AI as an opportunity to enhance their work.
Despite the marketing hype, Xbow's biggest bounty so far is just $3,000, which doesn’t even cover the costs of operating the tool. This further reinforces the idea that Xbow is not focused on bug bounties but on improving internal security at scale.
In conclusion, Xbow is not a job killer but a tool to augment human expertise in cybersecurity. AI like Xbow will help professionals identify vulnerabilities faster, but the human element remains indispensable for complex attacks. So, focus on building your skills, credentials, and adapting to new tools like Xbow to stay ahead in the cybersecurity field.
Subscribe to God Access Labs to stay updated with the latest trends and insights in the offensive security world.